In a nutshell: A security researcher recently uncovered nearly three dozen Chrome Web Store extensions exhibiting suspicious behavior. Many present themselves as search assistants, while others pose as ad blockers, security tools, or extension scanners – all mysteriously linked to a single, unused domain.
John Tucker, founder of browser security firm Secure Annex, discovered the suspicious extensions while assisting a client who had installed one or more for security monitoring. The first red flag: two of the 132 extensions he analyzed were unlisted, meaning they don’t appear in web searches or the Chrome Web Store. Users can only download these tools via a direct URL. Unlisted extensions aren’t that uncommon. Businesses sometimes use them to limit public access to internal tools.
However, malicious actors often use unlisted extensions to exploit users, keeping them hidden and making it difficult for Google to detect. After Tucker began analyzing the two suspicious extensions, he uncovered 33 more. Many connect to the same servers, use identical code patterns, and request the same permissions.
The apps ask users for consent to access sensitive data, including browser tabs and windows, cookies, storage, scripting, alarms, and management APIs. This level of access is unusually high, making it easy for bad actors to exploit the user’s system for various malicious purposes.
“At this point, this information should be enough for any organization to reasonably kick this out of their environment as it presents unnecessary risk,” Tucker wrote in his blog on Thursday. “The only permission any of the 35 apps requires is management,” he added in an email to Ars Technica.
In addition to the suspicious number of permissions these apps request, their programming is equally concerning. Tucker found the apps had heavily obfuscated code. A developer would only program their software this way to make it difficult for others to examine and understand its actions.
Collectively, users have installed the 35 apps over 4 million times. While it’s unclear how unlisted extensions attracted so much attention without appearing in searches, Tucker notes that 10 carried Google’s “Featured” tag – a designation typically given to developers Google has vetted and trusts. He didn’t elaborate on how this may have influenced their distribution.
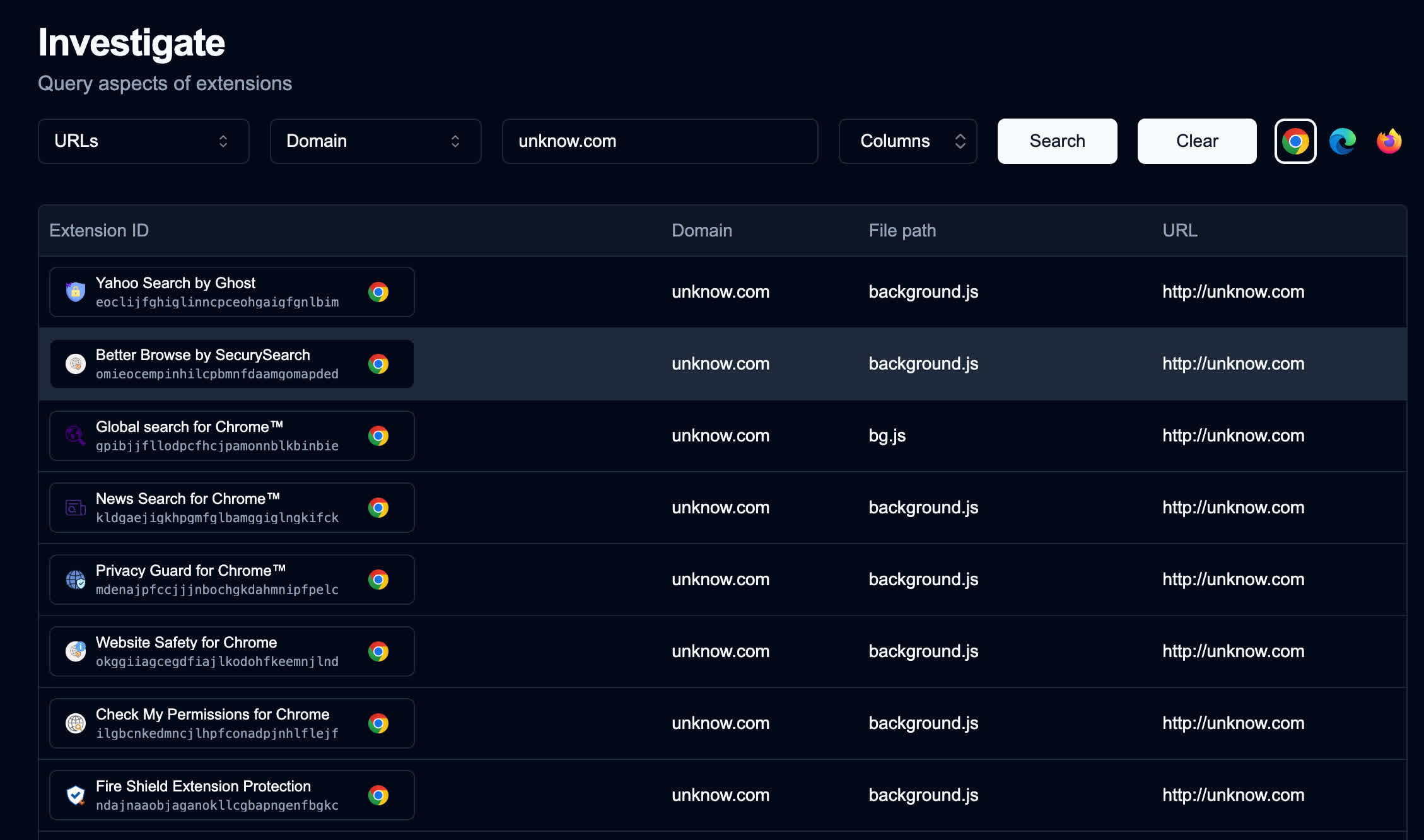
Tucker found no direct evidence that the extensions exfiltrate data – but that doesn’t rule it out. One tool called Fire Shield Extension Protection ironically claims to scan Chrome for malicious or suspicious plugins. After analyzing it, Tucker discovered a JavaScript file that can upload data and download code and instructions from several shady domains, including one called unknow.com.
This domain stands out because all 35 apps reference it in their background service daemons despite it having no visible web presence or clear function. Whois records list it as “available” and “for sale,” making it especially bizarre that so many extensions would point to it.
“Hilariously, the domain doesn’t have any relevance in the code, but [is] incredibly useful for linking all of the extensions together!” Tucker said.
Secure Annex published a comprehensive list of extension IDs and permhashes on its blog and in a publicly accessible spreadsheet. A simpler list of extension names appears in the image above. If you have any of these installed, Tucker recommends removing them immediately – the security risks far outweigh any potential benefit.